Xenomorph is a variant of a banker malware called Alien initially noted in February 2022. Later that year, this financial malware was able to bypass the security features of Android 13.
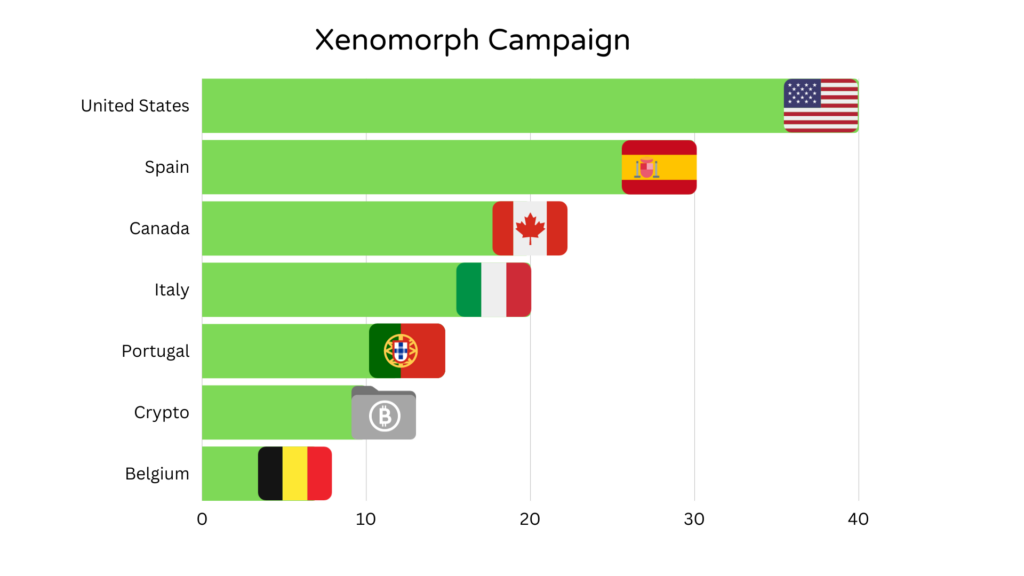
This year an updated version of this banking trojan has resurfaced as confirmed by Netherlands-based security research firm ThreatFabric. With new features, Xenomorph has enhanced its attack horizon in countries like the United States, Canada, Belgium, Italy, Portugal and Spain netting thousands of downloads.
The Automated Transfer System (ATS) framework is the power engine of this malware that allows its operators, Hadoken Security, to execute a chain sequence of actions to take full control of the infected devices.
The ATS framework can automatically access account balance information, extract credentials and obtain MFA tokens from authenticator apps. Subsequently, Xenomorph can initiate fund transfer requests without any need for a human user.
“Actors have put a lot of effort into modules that support Samsung and Xiaomi devices,” the ThreatFabric researchers said. “This makes sense, considering that these two combined make up roughly 50% of the whole Android market share.”
Users of the Google Chrome browser or Google Play store are usually less cautious when they see an update request by either of the platforms. Researchers found that Xenomorph’s distribution method is leveraging this faith by showing phishing pages (with malicious APK) as a Chrome update.
With dozens of new overlays for financial institutions, this Trojan is now able to target 25 financial applications used in Spain, 30 financial applications in the USA and around 15 banking applications in Canada. With these overlays, Xenomorph obtains Personally Identifiable Information (PII).
Moreover, the malware is capable of distributing desktop stealers like RisePro and Lumma C2. This indicates a threatening phenomenon—Xenomorph is officially sold as a MaaS (Malware as a Service).
What are the Updated Features?
- Anti-sleep: This new version of Xenomorph has added several new commands. One of which is show_push (Enable anti-sleep push notification). This feature prevents the sleep function of the infected device by enabling an active push notification.
- Mimic: Two more newly added commands are start_mimic (start mimic function) and stop_mimic (stop mimic function). The threat actor can act like any other legitimate application by hiding one significant pattern that is associated with malware. An activity called IDLEActivity can display a legitimate website as a WebView.
- Click On Point: This is executed through a command clickOnPoint. Through this command, Xenomorph can simulate touch at specific coordinates that allow it to carry out small actions without the deployment of the full ATS module.
After months of hiatus, Xenomorph is back and still holds its standing as an awfully threatening Android Banking malware. Criminal minds behind this malware have put a lot of effort into perfecting this product and expanding its reach.
“The fact that we saw Xenomorph being distributed side-by-side with powerful desktop stealers is very interesting news. It could indicate a connection between the threat actors behind each of these malware, or it could mean that Xenomorph is being officially sold as a MaaS to actors, who operate it together with other malware families. In each case, it indicates an activity from Xenomorph which we have not seen before, but which we might see a lot of in the near future”—ThreatFabric concludes.

