Cryptocurrency users have been warned to be more cautious while logging into reputable cryptocurrency platforms using mobile devices. Cybersecurity analysts have spotted a new phishing kit that targets users by impersonating the login pages of established and well-known cryptocurrency services.
This novel attack vector is so advanced that it fakes the login screen only after users complete a CAPTCHA test using hCaptcha. This effectively neutralizes automated security analysis tools that are in place to safeguard users’ interests.
“This kit enables attackers to build carbon copies of single sign-on (SSO) pages, then use a combination of email, SMS, and voice phishing to trick the target into sharing usernames, passwords, password reset URLs, and even photo IDs from hundreds of victims, mostly in the United States,” Lookout said in a report.
There are also instances where these pages hoaxed a user via unsolicited phone calls or text messages mimicking the crypto platform’s customer support under the context of securing a vulnerable account. When the user enters the credentials the phishing kit asks for two-factor authentication (2FA) code.
Once the user enters the one-time password (OTP), the threat actor instantly captures it. Subsequently, the victim is directed to any page the attack vector wants.
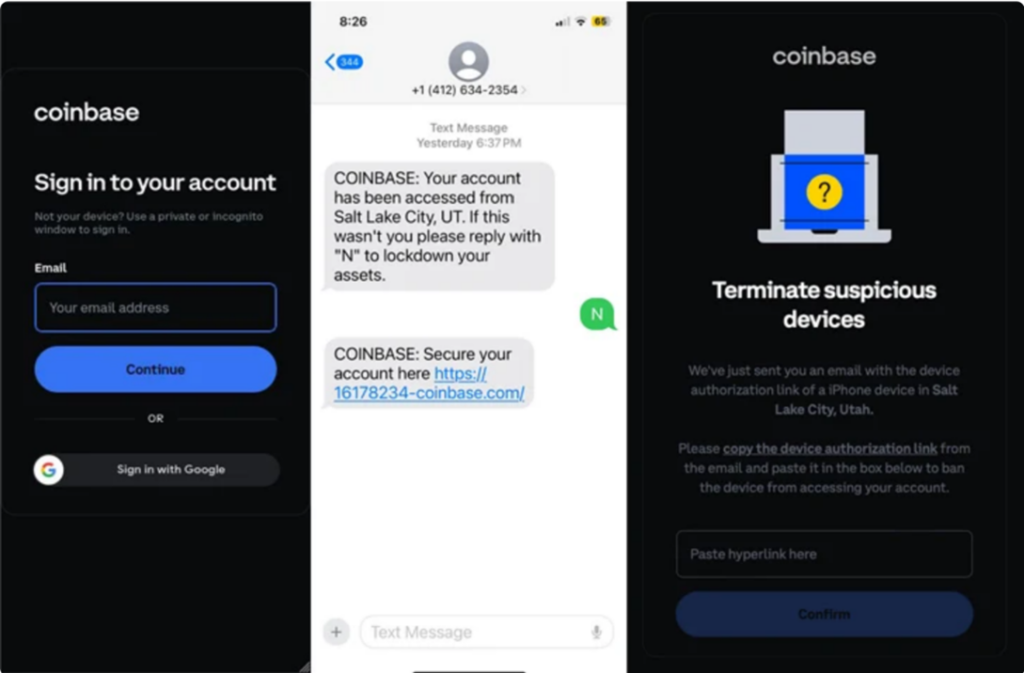
To combat any suspicion that may come into users’ minds, the novel phishing kit allows the operator to customize the phishing page in real-time. This is done by providing the last 2 digits of the victim’s legitimate phone number or selecting whether the victim should be asked for a six or seven-digit token.
“The attacker likely attempts to log in using these credentials in real time, then redirects the victim to the appropriate page depending on what additional information is requested by the MFA service the attacker is trying to access,” Lookout said.
It is still vague if this attack vector works independently or if it is a part of any existing attack groups. However, the attacks are designed to target employees of Binance, Coinbase, Federal Communications Commission (FCC), and popular platforms like Gemini, Kraken, Trezor and ShakePay. So far, it has been reported that more than 100 victims are phished.
“The combination of high-quality phishing URLs, login pages that perfectly match the look and feel of the legitimate sites, a sense of urgency, and consistent connection through SMS and voice calls is what has given the threat actors so much success stealing high-quality data,” Lookout noted.
Security analysts first took note of this new phishing toolkit when Fortra revealed that several financial institutions in Canada experienced a new phishing-as-service (PhaaS) attack by a group called LabHost.
“LabHost services allow threat actors to target a variety of financial institutions with features ranging from ready-to-use templates, real-time campaign management tools, and SMS lures,” Lookout added.

