“Any enterprise or individual that is serving an HTTP-based workload to the Internet may be at risk from this attack”, warned Google.
In the second week of October, Cloudflare, AWS and Google were hit by the largest distributed denial-of-service (DDoS) attacks in the history of internet. The ground-breaking attack was based on a novel technique called HTTP/2 Rapid Reset Zero Day by an unknown threat actor. Interestingly, HTTP/2 protocol is used by a large number of web servers—77% to be exact as per Web Almanac. So, the severity of the attack was enormous.
Back in August 2023, Cloudflare detected layer 7 attacks with susceptibility tracking as CVE-2023-44487. The CVSS score was 7.5 out of 10. Cloudflare recently experienced an HTTP/2 Rapid Reset DDoS campaign that peaked at 201 million Requests Per Second (RPS)–three times higher than the 71 million RPS they encountered back in February this year.
For Amazon AWS, the largest peak was at 155 million RPS over the span of two days while for Google it was 398 million RPS in a single day.
How HTTP/2 Rapid Reset Works
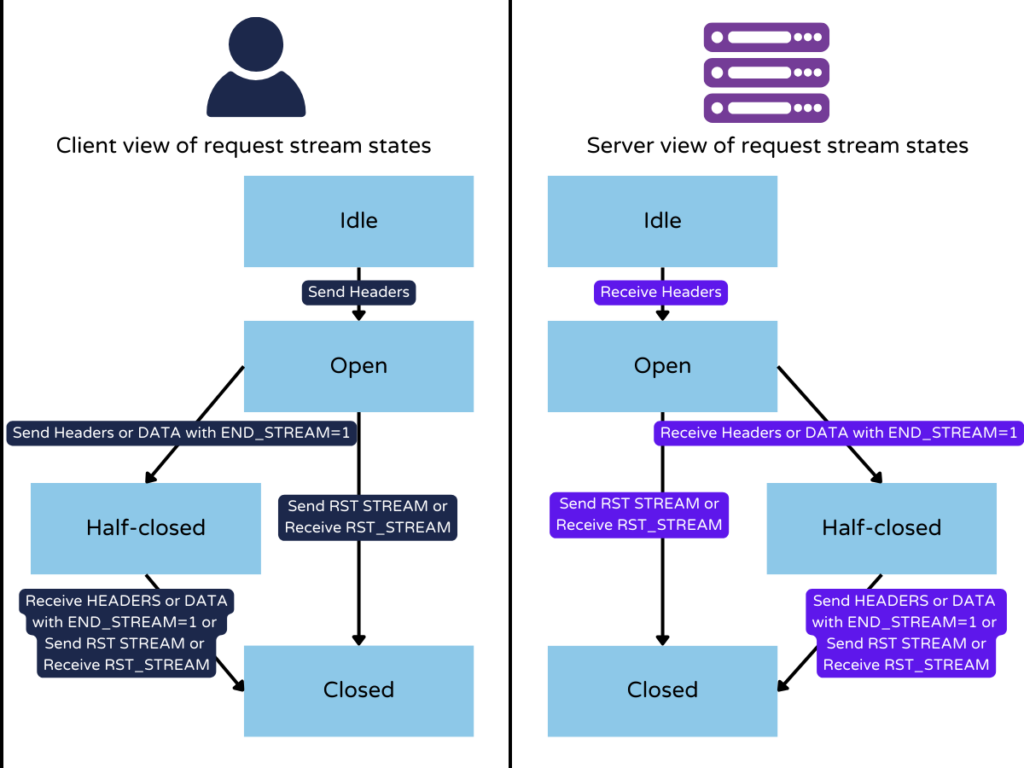
The attack vector abuses a zero-day flaw in the HTTP/2 protocol termed ‘stream cancellation’ by recurrently sending a request and terminating it immediately. More elaborately, if a client decides to abort a request an ‘RST_STREAM frame’ is issued. The Rapid Reset capitalizes this command by sending and canceling requests in rapid succession.
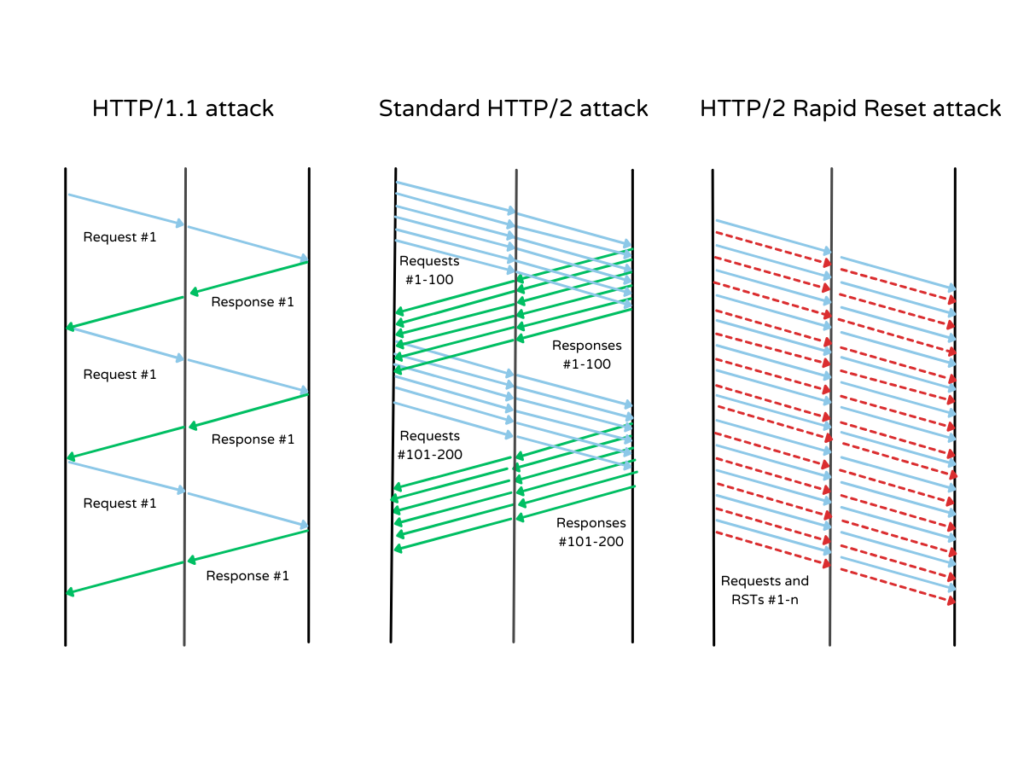
Thus, the attack vector sidesteps the server’s concurrent stream and overloads the server with a fake threshold. When this happens at scale, the threat actor can engulf any website and knock it offline. With a botnet of only 20,000 compromised devices, this largest attack shook the internet giants. This number is far less than normal regular attacks that usually comprise hundreds of thousands or even millions of machines.
“By automating this trivial ‘request, cancel, request, cancel’ pattern at scale, threat actors are able to create a denial of service and take down any server or application running the standard implementation of HTTP/2,” Cloudflare explained.
What companies are saying?
After the initial DDoS attacks, Google observed multiple variants of the Rapid Reset. Although these variants are not as threatening as the initial version, they are still more efficient than standard HTTP/2 DDoS attacks.
All three companies said that their current security measures were able to handle HTTP/2 with lesser damage. However, they have implemented additional steps for fending off such attack patterns. Subsequently, all web server software companies have started developing patches and implementing them across the servers to prevent exploitation.
F5, an independent advisory, urged their customers to update the current NGINX configuration as the attack impacted the NGINX HTTP/2 module. Updating the configuration will limit the number of simultaneous streams to a default of 128 and stick with HTTP connections for up to one thousand requests.
“To protect your systems from this attack, we’re recommending an immediate update to your NGINX configuration,” F5 wrote.